I participated in a Twitter chat today and was asked "A Blade Runner-type debate. What is it to be human? Believe always on connectivity is changing us & emotions"
My comment was that "Connectivity is so much part of our lives! Have we evolved?"
Let me elaborate...
When I was growing up a million years ago, I watched too much television. I would spend around 3 hours a day in front of three terrestrial channels, as I grew up I was given an Apple II at 12, and an Atari ST when I was 15 and eventually my first PC when I was 20. Access to the internet when I was 23 at work, AOL at home when I was 24, home broadband when I was 26 and home wireless when I was 30.
Things moved on to the point where I now have, a work laptop, my personal laptop, a Nexus 7 tablet and a HTC One M8. The house has two computers in the kitchen (which the children use for homework and Minecraft), a tablet for each of my older two children, an iPad 2 being used by the youngest two children, and a Chromebook and a Moto G smartphone for my wife. I'm not even counting the PS3, Wii or DS Lites.
I think it's fair to say we have embraced technology in our household.
My children spend a similar amount of time in front of a screen as I did, but now the content is dynamic, rather than the three channels of stuff you couldn't choose.
Evolution, not wanting to get into a debate but it doesn't always mean it's for the best, but rather a change typically caused by environment. The level of connectivity has changed our lives, whether it's gathering information, communicating, entertainment, shopping, checking the news and weather, finding a restaurant, looking for reviews, education, etc, etc.
I remember speaking to a couple a few years ago and they didn't have the internet at home. The school told them that if they didn't get it soon, it would impact on their children's education. You can see the schools concern when we consider what we take for granted by having the internet.
Is this what it is to be human now? Is connectivity a human right or an essential utility? Are we talking about First World Issues? Have we truly evolved? Do humans dream of analogue sheep?
Wednesday, 3 December 2014
FutureLearn: Introduction to Cyber Security (Week 1-8)
After being incredibly proud of myself for completing the online learning around programming, I thought I'd look at other courses as well.
I found one run by the Open University giving an "Introduction to Cyber Security". As some of you know I work in this field, so what's the point of doing this course?
Most importantly to some, it's a free course! But also I wanted to ensure my knowledge was relevant and current, which reassuringly it was. I also wanted to see the material and see if it would be of use for others. Again, I found the course well structured and the segments within each weeks learning broken down into bite size chunks.
I know a few people in the IT security industry who are assumed to have the basic knowledge. This course can ensure they do have that knowledge. Whether you're completely new to IT security, or want a refresher, it's certainly useful.
The course recommends setting aside 3 hours per week, for the duration of the eight week course. I managed to complete the course within a couple of evenings, but I have over 8 years working with IT security and a number of IT certifications which regularly teaches and tests this knowledge.
I found one run by the Open University giving an "Introduction to Cyber Security". As some of you know I work in this field, so what's the point of doing this course?
Most importantly to some, it's a free course! But also I wanted to ensure my knowledge was relevant and current, which reassuringly it was. I also wanted to see the material and see if it would be of use for others. Again, I found the course well structured and the segments within each weeks learning broken down into bite size chunks.
I know a few people in the IT security industry who are assumed to have the basic knowledge. This course can ensure they do have that knowledge. Whether you're completely new to IT security, or want a refresher, it's certainly useful.
The course recommends setting aside 3 hours per week, for the duration of the eight week course. I managed to complete the course within a couple of evenings, but I have over 8 years working with IT security and a number of IT certifications which regularly teaches and tests this knowledge.
Tuesday, 2 December 2014
FutureLearn: Begin Programming: Build your first mobile game (Week 7)
Well the seven weeks have flown by and this is the final week of my FutureLearn course.
The course and material was very well structured, and I leave understanding more about the process of programming. Am I am to make my own mobile app... well not without a little more work, but I certainly understand the process to do this.
There was a test at the end of the course, which was pretty straightforward, if you paid attention for the previous six weeks.
The online learning process was an interesting one for me, and I will look at other courses to learn some new things!
Good luck if you want to start programming, and this is an excellent way to start!
The course and material was very well structured, and I leave understanding more about the process of programming. Am I am to make my own mobile app... well not without a little more work, but I certainly understand the process to do this.
There was a test at the end of the course, which was pretty straightforward, if you paid attention for the previous six weeks.
The online learning process was an interesting one for me, and I will look at other courses to learn some new things!
Good luck if you want to start programming, and this is an excellent way to start!
Monday, 1 December 2014
Where Does the Buck Stop In Newsworthy Breach? [Link - Business Value Exchange]
I participated in a Cyber Governance Twitter chat where my comment was used as part of the blog summary:
http://businessvalueexchange.com/blog/2014/12/01/buck-stop-newsworthy-breach-cyber-governance-twitter-chat-summary/
http://businessvalueexchange.com/blog/2014/12/01/buck-stop-newsworthy-breach-cyber-governance-twitter-chat-summary/
Saturday, 29 November 2014
The development of standards for the Internet of Things (IoT) [Link - Computer Weekly]
I was recently asked for my comments for a magazine article around whether the Internet of Things (IoT) could be standardised.
As you can image, I give a number of comments to the press, but it's always good to see them being used: http://www.computerweekly.com/feature/How-the-development-of-standards-will-affect-the-internet-of-things
As you can image, I give a number of comments to the press, but it's always good to see them being used: http://www.computerweekly.com/feature/How-the-development-of-standards-will-affect-the-internet-of-things
FutureLearn: Begin Programming: Build your first mobile game (Week 5 & 6)
I had a few things on at work, so my studying slipped and had to catch up two weeks of course material this week.
Again, it this may have been more of a challenge for those who have never programmed before, but fortunately I could leverage previous experiences.
Week 5 was about algorithms, and week 6 about functions. Both areas have been touched upon in previous weeks, but certainly well developed course material around these subjects. The mix of theory and practicals make it feel like a more complete learning experience.
Next weeks course will be the last one in this series, so I'll see how that goes then.
Again, it this may have been more of a challenge for those who have never programmed before, but fortunately I could leverage previous experiences.
Week 5 was about algorithms, and week 6 about functions. Both areas have been touched upon in previous weeks, but certainly well developed course material around these subjects. The mix of theory and practicals make it feel like a more complete learning experience.
Next weeks course will be the last one in this series, so I'll see how that goes then.
Tuesday, 25 November 2014
Comments about Darktrace [Link - The Guardian]
I was asked my opinion on the Darktrace solution by the Guardian:
http://www.theguardian.com/technology/2014/nov/25/government-malware-nsa-hacker-cyber-attacks
http://www.theguardian.com/technology/2014/nov/25/government-malware-nsa-hacker-cyber-attacks
Sunday, 16 November 2014
FutureLearn: Begin Programming: Build your first mobile game (Week 4)
This week we looked at loops and arrays, which again I remember from my programming days at university. The videos and tutorials were excellent, giving a great reminder on how to tackle these elements and where they are used.
Tuesday, 11 November 2014
FutureLearn: Begin Programming: Build your first mobile game (Week 3)
This week was learning about conditional statements. Again there was familiarity with reading the code and understanding the statements, which helped speed up this weeks learning. There is still plenty to learn from a syntax perspective, but not as hard as I thought it may be.
Thursday, 6 November 2014
FutureLearn: Begin Programming: Build your first mobile game (Week 2)
This week was spent learning about code constructs. It covered off data types and variables, as well as operators and precedence.
It seems that the Pascal programming I did at university over 20 years had stuck, as this week made a lot of sense and was very familiar.
Next week is covering conditional statements, which I think I remember as well!
It seems that the Pascal programming I did at university over 20 years had stuck, as this week made a lot of sense and was very familiar.
Next week is covering conditional statements, which I think I remember as well!
PS3 Hard Drive Upgrade
A bit of a departure from the type of topics I normally blog about!
My slim PS3 is about five years old and really only used for a couple of reasons. It's my blu-ray player, and we use it for Singstar! I noticed that with the new version of Singstar, the game was hanging and the PS3 running hot.
Being cautious, I took a back up of the existing 160GB hard drive onto an external USB hard drive. The total size of the back up was 60GB, so the storage is really being used. I notice that the drive was quite noisy as well, so I decided the replacement drive should be an SSD (solid state drive). With no moving parts it will not generate the same amount of heat or noise as a traditional hard drive. It should be quicker as well and from some of the comments online, it may remove some of the lag in bigger games.
Rather than replace the drive with a larger capacity drive, I opted for a smaller one to get the SSD at a price point below £40 for 128GB.
I followed these instructions to remove the existing drive and drop in the new one:
http://uk.playstation.com/ps3/support/general/detail/linked347570/item347531/Replacing-the-hard-disk-(other-models)/
With a blank drive in place the PS3 will complain about not having system software on the drive. The system software can be downloaded from here: http://uk.playstation.com/ps3/
Once downloaded, get a USB stick or USB drive and plug it into your computer. Create a folder on the root of the drive called PS3 (and ensure it's in upper case). In that folder, create another folder called UPDATE (again in upper case) and then copy the file into that folder.
Plug the USB device into the PS3, and you will need to use a controller connected by a USB cable as well. When prompted, press and hold the Start and Select buttons together. It will then prompt you that the hard drive will need to be formatted, which is initiated by pressing and holding the Start and Select buttons for five seconds.
Once formatted, it will copy the System Software onto the hard drive and you will have to run through the initial setup of the PS3 again. Once completed, you will be able to restore from the backup file created initially to get all the games and saves back.
I now have a quick and silent PS3, which should hang mid game for a while!
My slim PS3 is about five years old and really only used for a couple of reasons. It's my blu-ray player, and we use it for Singstar! I noticed that with the new version of Singstar, the game was hanging and the PS3 running hot.
Being cautious, I took a back up of the existing 160GB hard drive onto an external USB hard drive. The total size of the back up was 60GB, so the storage is really being used. I notice that the drive was quite noisy as well, so I decided the replacement drive should be an SSD (solid state drive). With no moving parts it will not generate the same amount of heat or noise as a traditional hard drive. It should be quicker as well and from some of the comments online, it may remove some of the lag in bigger games.
Rather than replace the drive with a larger capacity drive, I opted for a smaller one to get the SSD at a price point below £40 for 128GB.
I followed these instructions to remove the existing drive and drop in the new one:
http://uk.playstation.com/ps3/support/general/detail/linked347570/item347531/Replacing-the-hard-disk-(other-models)/
With a blank drive in place the PS3 will complain about not having system software on the drive. The system software can be downloaded from here: http://uk.playstation.com/ps3/
Once downloaded, get a USB stick or USB drive and plug it into your computer. Create a folder on the root of the drive called PS3 (and ensure it's in upper case). In that folder, create another folder called UPDATE (again in upper case) and then copy the file into that folder.
Plug the USB device into the PS3, and you will need to use a controller connected by a USB cable as well. When prompted, press and hold the Start and Select buttons together. It will then prompt you that the hard drive will need to be formatted, which is initiated by pressing and holding the Start and Select buttons for five seconds.
Once formatted, it will copy the System Software onto the hard drive and you will have to run through the initial setup of the PS3 again. Once completed, you will be able to restore from the backup file created initially to get all the games and saves back.
I now have a quick and silent PS3, which should hang mid game for a while!
Monday, 3 November 2014
Building Your Business’ Best Defence Against Cyber-Threats [Link - Fresh Business Thinking]
It is increasingly very difficult for businesses to respond to security threats. Gradually, threats have become more sophisticated, blending different levels and methods of attacks which have made it more and more difficult for IT departments to respond to them appropriately. With IT budgets driven down in some sectors, the problem has been exacerbated: defences are weakened and the attacks are gaining strength and detail.
The biggest security challenge for businesses is looking at the basic threats facing them and securing against these vulnerabilities. The first consideration is whether a business’ website is protected. IT departments should also review the protocols in place to prevent existing or ex-employees from accessing sensitive company data. Businesses often worry about what brand of firewall they should be using, when the most basic protection against internal breaches has not been dealt with. A lock is useless when you've left the door wide-open!
Responding to a security threat will rely heavily on preparation. To ensure you are ready to respond at a moment’s notice, consider the following:
1. Think about the business strategy to respond to threats before they hit
2. Review your current vulnerabilities and form an action plan
3. Consider further staff training and education
4. Only consider new technology/software once you have addressed the ‘person factor’
Overcoming security threats is about getting the basics right, and recognising that often the biggest threat to a business is people, whether intentionally or not. People make mistakes, they can be manipulated, or they can simply hold a grudge. Never underestimate the threat that individuals, both external and internal to a business, can pose.
Thus often the best prevention for a security breach is not simply identifying glaring vulnerabilities, but rather looking at where the 'lure' for the potential hacker or person wishing to do damage is. Googling oneself is not about vanity, but in fact it can actually help to protect a business online. If an employee’s social media presence details pet names, kids names, hobbies etc., then a business could find that 'password reminders' are suddenly available for the tenacious hacker looking to do damage.
Ultimately, the first solution to cyber threats is to look at the people involved, the company’s profile, and its website – and only once that has been considered should software/hardware solutions to support this be considered.
http://www.freshbusinessthinking.com/articles_print.php?CID=3&AID=13615
The biggest security challenge for businesses is looking at the basic threats facing them and securing against these vulnerabilities. The first consideration is whether a business’ website is protected. IT departments should also review the protocols in place to prevent existing or ex-employees from accessing sensitive company data. Businesses often worry about what brand of firewall they should be using, when the most basic protection against internal breaches has not been dealt with. A lock is useless when you've left the door wide-open!
Responding to a security threat will rely heavily on preparation. To ensure you are ready to respond at a moment’s notice, consider the following:
1. Think about the business strategy to respond to threats before they hit
2. Review your current vulnerabilities and form an action plan
3. Consider further staff training and education
4. Only consider new technology/software once you have addressed the ‘person factor’
Overcoming security threats is about getting the basics right, and recognising that often the biggest threat to a business is people, whether intentionally or not. People make mistakes, they can be manipulated, or they can simply hold a grudge. Never underestimate the threat that individuals, both external and internal to a business, can pose.
Thus often the best prevention for a security breach is not simply identifying glaring vulnerabilities, but rather looking at where the 'lure' for the potential hacker or person wishing to do damage is. Googling oneself is not about vanity, but in fact it can actually help to protect a business online. If an employee’s social media presence details pet names, kids names, hobbies etc., then a business could find that 'password reminders' are suddenly available for the tenacious hacker looking to do damage.
Ultimately, the first solution to cyber threats is to look at the people involved, the company’s profile, and its website – and only once that has been considered should software/hardware solutions to support this be considered.
http://www.freshbusinessthinking.com/articles_print.php?CID=3&AID=13615
Friday, 31 October 2014
Giving blood...
A dear friend of mine is amazing! Why? Have a read of her story...
http://www.hopegoesupanddown.blogspot.co.uk/
Her husband was knocked off his bike in London and suffered a major brain injury. During his operations Jake required a lot of blood. Since finding this out, I decided to give blood and try to be a regular donor.
Here's my fourth donation, with my fifth one planned for February. It's always easy to make an excuse not to do it, but re-reading Charlie's blog not only inspires me with what human spirit and strength truly is, but it also reminds me that a small act on my part can save a life.
Do something amazing and find out if you can give blood: http://www.blood.co.uk/
http://www.hopegoesupanddown.blogspot.co.uk/
Her husband was knocked off his bike in London and suffered a major brain injury. During his operations Jake required a lot of blood. Since finding this out, I decided to give blood and try to be a regular donor.
Here's my fourth donation, with my fifth one planned for February. It's always easy to make an excuse not to do it, but re-reading Charlie's blog not only inspires me with what human spirit and strength truly is, but it also reminds me that a small act on my part can save a life.
Do something amazing and find out if you can give blood: http://www.blood.co.uk/
Sunday, 26 October 2014
FutureLearn: Begin Programming: Build your first mobile game (Week 1)
A friend posted a link on Facebook about an online training course to an Introduction to Forensic Science. Sounds like great fun ,if you're a CSI fan, like I am, but I delved a little deeper to see what other courses were available.
All the courses are free and seem to be run by reputable universities. The courses are structured to be carried out over a few weeks, requiring a few hours that week. I chose the "Begin Programming: Build your first mobile game" as my first course. It runs for 7 weeks, requiring around 3 hours per week depending on your level of experience. I haven't programmed since I was in university, so thought it may be fun to see what programming is like 20 years on!!
There is a need to register on the site, but nothing too horrific! This course was already underway, but as it was only week 1, there was still time to catch up before week 2's content was released.
The first week required the installation covered off a number of elements, including:
All the courses are free and seem to be run by reputable universities. The courses are structured to be carried out over a few weeks, requiring a few hours that week. I chose the "Begin Programming: Build your first mobile game" as my first course. It runs for 7 weeks, requiring around 3 hours per week depending on your level of experience. I haven't programmed since I was in university, so thought it may be fun to see what programming is like 20 years on!!
There is a need to register on the site, but nothing too horrific! This course was already underway, but as it was only week 1, there was still time to catch up before week 2's content was released.
The first week required the installation covered off a number of elements, including:
- An introduction to programming
- How to use the FutureLearn website
- Software requirements for the course
- How to download & install the JDK
- How to download & install the Android SDK
- How to download the game framework for the course
- Setting up the IDE
- Setting up the game and running it
- Understanding the Android folder system
- Setting up the game on an Android device
I ran through the above, and it took around three hours. I had a couple of glitches, as the original course didn't allow for the release of Android 5.0 Lollypop in mind, and so there were some changes required for the Android SDK. It took me a couple of goes to get it right. Although a little frustrating, it was not the fault of the course, when Google update software! That said, the content so far has been great and certainly at right pace for someone who is not a programmer.
Saturday, 4 October 2014
Social Engineering - The Art of Deception
After a friend read my blog post about securing your virtual identity, he recommended that I read the book "The Art of Deception: Controlling the Human Element of Security" by Kevin Mitnick, which can be purchased from Amazon.
The book is structured with stories and anecdotes about how people have fallen for social engineering, and what lessons can be learnt from these situations. Having worked in an IT security environment for nearly a decade, I am aware of vendor and technical solutions to tackle issues that IT environments without security measures.
Growing up I watched a number of films, including the likes of Wargames, Hackers, The Net and Swordfish. They may not be great films, but they gave a romantic view of hacking. I was interested in this realm of IT when I first started my career nearly two decades ago, but I'd say I was a failed script kiddie. I didn't understand the systems well enough to penetrate the security measures, and struggled to get the tools to work correctly.
I'd hear the stories of social engineering conquests and I'm in awe of the confidence and arrogance to manipulate people to test an organisations security! Reading this book shows how easy it is to manipulate people and how easy it is to have them carry out tasks in isolation that seem so insignificant, but when couple with a number of tasks, you have all the pieces of a jigsaw to manipulate a company!
The book was incredibly easy to read and even though I'm not a big reader, I finished it in less than two days. It's real page turner, and even though it was written nearly 12 years ago it is still very relevant. If you just read the book about what you shouldn't do, anyone with IT security awareness will tell you they have been told this already. Taking the story of the manipulation and how to con worked and why is eye opening.
The book ends on how to create a security awareness program, including how to train staff. Following all the advice will not mean you are secure, but it will certainly help and have people think about who is requesting the action. All the technology in the world will not secure you and your organisation, but stopping the people from being the weak link will certainly help.
Friday, 26 September 2014
Shellshocked!
What is Shellshock?
It has been
widely reported in mainstream news that vulnerability dubbed Shellshock could
affect 500 million devices, which over shadows the 500,000 devices that were
affected by the Heartbleed vulnerability.
Shellshock
exploits a vulnerability in a command line shell used by many UNIX computers,
called the Bourne Again Shell, more commonly known by its acronym Bash. This affects computers and devices using the Linux
and Mac OS, including some appliance based devices such as firewalls, which are
commonly built on Linux.
Bash is a
common component in webservers, but even if Linux is not being used, Apache
also uses Bash. It could also be used as
a background component for web browsers, email clients and file transfer
applications.
Whereas
Heartbleed was a vulnerability that allowed the traffic to be sniffed, the
Shellshock vulnerability allows direct access on to the vulnerable machine and
with potentially three lines of code.
More technical details around the vulnerability CVE-2014-6271 aka Shellshock is linked.
What can be done?
Patch the
Linux and Mac OS machines to the latest version. There are rumours that due to the speed of
patch dispatch, they may not have been QA’d as thoroughly, but it is still
better than being vulnerable.
Remember that
devices other than computers and servers running Linux or Mac OS can be
affected. Ensure your client software is
up to date, regardless of the operating system.
With devices such as firewalls, check regularly on the vendor websites
for their advice.
Here is the latest government advice on the Bash vulnerability
Here is the latest government advice on the Bash vulnerability
I’m checking
the vendor sites that MTI Technology partners with and slowly creating a list
of useful links here:
Cisco
http://www.cisco.com/web/about/security/intelligence/Cisco_ERP_Bash_09252014.html
Cryptzone
https://support.cryptzone.com/hc/en-us/articles/201543171-Statement-regarding-Shell-Shock-Vulnerability
EMC
http://support.emc.com/kb/192608
ExtraHop
http://www.extrahop.com/post/blog/monitor-shellshock-attempts-with-extrahop/
F5
https://devcentral.f5.com/articles/cve-2014-6271-shellshocked
GTA (Global Technology Associates)
http://forum.gta.com/forum/user-community-support/firewall-general/1533-bash-shellshock-vulnerability-cve-2014-6271
Imperva
http://blog.imperva.com/2014/09/shellshock-vulnerability-cve-2014-6271.html
Juniper
http://kb.juniper.net/InfoCenter/index?page=content&id=JSA10648
Lumension
https://www.lumension.com/kb/Home/General-Information/1666-(1).aspx
McAfee
https://kc.mcafee.com/corporate/index?page=content&id=SB10085
MobileIron
http://www.mobileiron.com/en/smartwork-blog/mobileiron-not-vulnerable-bash-exploit
Cryptzone
https://support.cryptzone.com/hc/en-us/articles/201543171-Statement-regarding-Shell-Shock-Vulnerability
EMC
http://support.emc.com/kb/192608
ExtraHop
http://www.extrahop.com/post/blog/monitor-shellshock-attempts-with-extrahop/
F5
https://devcentral.f5.com/articles/cve-2014-6271-shellshocked
GTA (Global Technology Associates)
http://forum.gta.com/forum/user-community-support/firewall-general/1533-bash-shellshock-vulnerability-cve-2014-6271
Imperva
http://blog.imperva.com/2014/09/shellshock-vulnerability-cve-2014-6271.html
Juniper
http://kb.juniper.net/InfoCenter/index?page=content&id=JSA10648
Lumension
https://www.lumension.com/kb/Home/General-Information/1666-(1).aspx
McAfee
https://kc.mcafee.com/corporate/index?page=content&id=SB10085
MobileIron
http://www.mobileiron.com/en/smartwork-blog/mobileiron-not-vulnerable-bash-exploit
Palo Alto
Radware
https://drive.google.com/file/d/0B0zPUWiKiUjRUmJlSnFmaEsyeW8/edit?usp=sharing
RSA
https://knowledge.rsasecurity.com/scolcms/knowledge.aspx?solution=a67980
Sophos
http://www.sophos.com/en-us/support/knowledgebase/121444.aspx
Trend Micro
https://drive.google.com/file/d/0B0zPUWiKiUjRUmJlSnFmaEsyeW8/edit?usp=sharing
RSA
https://knowledge.rsasecurity.com/scolcms/knowledge.aspx?solution=a67980
Sophos
http://www.sophos.com/en-us/support/knowledgebase/121444.aspx
Trend Micro
http://esupport.trendmicro.com/solution/en-US/1105233.aspx
VMware
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2090740
VMware
http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=2090740
WatchGuard
Websense
http://www.websense.com/support/article/kbarticle/BASH-Shellshock-CVE-2014-6271
Westpoint
https://drive.google.com/file/d/0B0zPUWiKiUjRaC1zS3U4cWZrUGM/edit?usp=sharing
Xirrus
http://www.xirrus.com/blog/September-2014/Does-ShellShock-Vulnerability%E2%80%9D-impact-Xirrus-Custo
Here is the advice from some of the operating systems affected:
Apple
http://support.apple.com/kb/HT6495
CentOS
http://lists.centos.org/pipermail/centos/2014-September/146099.html
Debian
https://packages.debian.org/sid/bash
RedHat
https://access.redhat.com/solutions/1207723
Ubuntu
http://www.ubuntu.com/usn/usn-2362-1/
Westpoint
https://drive.google.com/file/d/0B0zPUWiKiUjRaC1zS3U4cWZrUGM/edit?usp=sharing
Xirrus
http://www.xirrus.com/blog/September-2014/Does-ShellShock-Vulnerability%E2%80%9D-impact-Xirrus-Custo
Here is the advice from some of the operating systems affected:
Apple
http://support.apple.com/kb/HT6495
CentOS
http://lists.centos.org/pipermail/centos/2014-September/146099.html
Debian
https://packages.debian.org/sid/bash
RedHat
https://access.redhat.com/solutions/1207723
Ubuntu
http://www.ubuntu.com/usn/usn-2362-1/
Last updated: 11:45 01/10/2014
Thursday, 25 September 2014
Securing the virtual you
I blogged recently about the Cyber Kill Chain where I look at each of the steps. Many of the steps can be dealt with using technology, except one stage, the reconnaissance stage.
LinkedIn
Twitter
Facebook
Who's the target?
As the bad guys need to be more specific in targeting individuals, research is the key. Knowing who someone works for, who their friends are, their hobbies and pastimes, they all help construction a picture of the target. If you know your target, you can try to exploit it by sending emails with specific topics and links to lure your target to click on a link which can compromise their machine.Spear-Phishing
People who are normally target to a "spear-phishing" (if phishing is a wide indiscriminate attack to get users details, spear phishing is targeting a very group or an individual person) are people who will have more rights than a typical user. Why? Well I mentioned in previous posts that a compromise will involve administrative credentials 100% of the time. So the target will often be members of the executive team (who often have more rights than a user) or members of the IT team.Research/Googling?
How would I find out more about someone? Use Google (other internet search engines are available) and search for them. As an example, I'll use me and see what's available out there...
The second hit is for LinkedIn and most of the posts that follow are for a Singaporean racing driver (I'll give you a hint, I'm not a racing driver!). For those who are unfamiliar with LinkedIn, it's a social networking site for "professionals" effectively giving a CV online.
So following the link, it takes me to a number of people called Andrew or Andy Tang internationally, but LinkedIn handily gives a link at the top to refine this list to Andrew or Andy Tangs based in the United Kingdom.
So if you knew who I worked for (MTI by the way), then you'd know to click on the top link. If you didn't, then you probably won't target me! So now I can see a public profile of Andrew Tang, and even without a LinkedIn account I can gather a lot of information.
Now you know who I work for and have worked for, along with people who I must be linked with in some fashion, as people looking for my profile have also looked at these profiles. That already creates links with people or organisations I would potentially trust, or would not find odd if I received a communication from them. Additional information such as company websites and blogs may also be there and give more clues.
Google+/Blogger
Following out to the blog, it can be seen that the URL to my blog (that you're reading by the way, thank you) is http://blog.andytang.com which gives us similar information to the LinkedIn profile, as well as a link to my public LinkedIn profile. There is also a link to my Google+ profile as the blog use Blogger which is a Google company.
Information we already have like company and LinkedIn details. There is a link to Twitter, along with some people who have put me in their circles. Again, more people that I would not find odd if I received communications from them. Let's follow the link to Twitter...
No real insights here, except that I say I live in Surrey. That may have been assumed as current and previous employers are in Surrey as well.
WhoIs?
Maybe time to get a little cleverer! We know the domain I own andytang.com, so there must be some information around that domain. A WhoIs will find out who has registered this domain:
No real information here either!
I've tried looking for a Facebook page, but struggle to find myself, even if I spread the net wider with more information than can be found above. None of the profiles below are me, but then I have locked down my privacy settings.
I thought I'd try a different way to get to the profile. I know who Andrew Tang works for and I know they have a Facebook page. Having a quick look through would show up any posts Andrew Tang may have liked, and from there I can access the profile and gather more information:
This shows my Facebook privacy settings work!
Corporate Website
Most corporate websites have a who's who on it, but I'm not currently on it. Although if I were, it would probably show a photograph and a brief about me, which could uncover hobbies or pastimes.
So what?
A lot of information can be uncovered very quickly about people. If I were a target to an attack, I would hope that my privacy settings and IT awareness would help. If the communication was more targeted from people I know or around a hobby or pastime, I may well click on them.
Our virtual presence keeps growing, but do we keep tabs on what's out there. I did the above with no special access or logins. The only site that needed an account was Facebook, but the rest is there to be discovered.
Take the time to secure and protect your information, and make sure there's not too much out there.
Googling yourself is no longer about vanity, it's about security!
Tuesday, 16 September 2014
IoT putting security in the balance
My wife and I have recently taken to Fitbit, where we monitor our steps, calories burnt and now our weight.
If I were playing "buzzword bingo", I'd say we have taken the "quantified self" analysis seriously, as it brings "gamification" to the monitoring. Some would say that "gamification" would mean you'd take it less seriously, not more... and I'd say those people are not or have never been gamers!
We purchased the Fitbit Aria bathroom scales to measure weight and body fat, with ability to give an accurate BMW reading, if your height is stored correctly.
I realised that the IoT (Internet of Things) had entered our home, as I was connecting the scales to the home wireless network, and telling my wife to expect an email from the bathroom scales! The scales work by taking your weight, then connecting to the wireless network you configured it for, then it will upload that information to a website hosting your Fitbit portal, allowing that information to be displayed by a dashboard.
Although I'm pretty aware of security, it made me realise that I need to firewall the scales to only be able to communicate with the Fitbit website. It also made me realise how unprepared we are, whether domestically or commercially, for the Internet of Things. As the devices are more autonomous, where it decides when and what it will do, you realise traditional solutions don't work. I'd want the firewall solution to be aware of the device and restrict what it can do. So the scales will only take weight, and only sent weight information to my Fitbit profile, and if it were to do anything else, the firewall would stop it.
I have a more detailed IoT blog post planned, but in the mean time consider what your new toy can do on its own!
If I were playing "buzzword bingo", I'd say we have taken the "quantified self" analysis seriously, as it brings "gamification" to the monitoring. Some would say that "gamification" would mean you'd take it less seriously, not more... and I'd say those people are not or have never been gamers!
We purchased the Fitbit Aria bathroom scales to measure weight and body fat, with ability to give an accurate BMW reading, if your height is stored correctly.
I realised that the IoT (Internet of Things) had entered our home, as I was connecting the scales to the home wireless network, and telling my wife to expect an email from the bathroom scales! The scales work by taking your weight, then connecting to the wireless network you configured it for, then it will upload that information to a website hosting your Fitbit portal, allowing that information to be displayed by a dashboard.
Although I'm pretty aware of security, it made me realise that I need to firewall the scales to only be able to communicate with the Fitbit website. It also made me realise how unprepared we are, whether domestically or commercially, for the Internet of Things. As the devices are more autonomous, where it decides when and what it will do, you realise traditional solutions don't work. I'd want the firewall solution to be aware of the device and restrict what it can do. So the scales will only take weight, and only sent weight information to my Fitbit profile, and if it were to do anything else, the firewall would stop it.
I have a more detailed IoT blog post planned, but in the mean time consider what your new toy can do on its own!
Monday, 15 September 2014
Lockheed Martin Cyber Kill Chain
When I first saw the the Cyber Kill Chain, it wasn't actually the Cyber Kill Chain. What I saw was the Websense 7 Stages of Advanced Threats.
The Lockheed Martin Cyber Kill Chain states there are seven stages of a cyber attack, and your organisation can be protected, if the chain is stopped at any of the stages. The higher up the chain it can be stopped, the better the protection to your network.
The stages are as follows:
The Lockheed Martin Cyber Kill Chain states there are seven stages of a cyber attack, and your organisation can be protected, if the chain is stopped at any of the stages. The higher up the chain it can be stopped, the better the protection to your network.
The stages are as follows:
- Reconnaissance
- Weaponise
- Deliver
- Exploit
- Install
- Command & Control
- Act on Objectives
Websense 7 Stages of Advanced Threats
Websense have taken the phases above, and mapped them to the Websense 7 Stages of Advanced Threats.
Recon
Prior to a breach, some research (or recon) will need to be done. This research will include the company and its people. By way of checking yourself, a quick internet search of your organisation or you will bring up a lot of information. The use of LinkedIn helps pinpoint people to organisations, as well as organisations that work together. While Facebook and Twitter will help with hobbies and out of work activities.
Lure
If hobbies or working relationships are known, the lure containing information regarding hobbies or an organisation you work with will be of interest. The lures can use email and social media from seemingly trusted sources.Redirect
Emails and social media can contain links, which then redirect the target, scan a system or prompt for software to be installed.Exploit Kit
The links can be for compromised websites, where an exploit kit located there can scan the users computer for vulnerabilities. The exploit kit is effectively looking for a path into the computer.Dropper File
The dropper file is the malware that is used to infect the users computer. The software when executed can immediate start gathering data, it can sit dormant for a period of time to mask it's true intentions, or may be used to deliver malware in the future.Call Home
The malware can then call home, contacting a Command & Control server to receive instructions, or additional software and tools.Data Theft
What as the point of all of this effort? To steal data!Stopping the Attack
Not all attacks will contain will seven stages. Some attacks will only involve three of these stages, but it highlights the sooner in the chain the attack is prevented, the less damage that will be done to the network.
Working in a technical environment, I see a number of solutions that only focus on some of these stages, which is no good if the attack skips those steps. I have worked with the Websense solutions for over seven years, and see that their solutions can prevent attack at all levels (expect the "Recon", but no technical solution can prevent an attacker from carrying out an internet search on people or organisations!)
MTI is a Websense Platinum Partner in the UK, and can help secure your network against cyber attacks.
Compromise the security (looking back at the RSA breach)
I had an interesting conversation with family this weekend, where I was talking about securing iCloud using two-step verification. Someone mentioned that with personal data it's not really important, but from a work perspective (they use to work for a large US company based globally) that RSA tokens protected them.
Back in 2011, RSA was compromised and is pretty much well documented. As a summary, here's happened:
Back in 2011, RSA was compromised and is pretty much well documented. As a summary, here's happened:
- Targeted emails were sent to the HR team at RSA
- Prior to the compromise only 11 emails were sent, but all of them were caught by the SPAM filtering solution
- One of these emails were released to the HR team as it looked important
- When the attachment was opened, it installed malware onto the computer exploiting a vulnerability in an Adobe product
- With this access, the hackers were able to pivot onto other servers, eventually getting to the token database, allowing them to generate the "secret" code of a token with a specific serial number
This breach is said to have cost RSA $66 million, but beyond the actual costs, there reputation of RSA as a security vendor was brought into question. It seems that this wasn't the end goal of the hackers, but rather the start to something much more spectacular!
Lockheed Martin is supplies military and aerospace technology to a number of organisations, including the Pentagon. This in itself would make Lockheed Martin an obvious target for attackers, but as an organisation concerned about security, they used RSA tokens to protect their network.
It would seem that Lockheed Martin were potentially victim to a state-sponsored attack from the Chinese government. Knowing that the target organisation were protected with RSA tokens, make it difficult to compromise them. Much easier would be have access to the RSA tokens, or at least the codes it would generate.
I appreciate that it is speculation that the Chinese nation state were behind the attack, but I would suggest that you do an internet search for two images and play "spot the difference":
- Lockheed Martin F-22
- Chengdu J-20
After the breach, Lockheed Martin created the Cyber Kill Chain, which shows the various steps of a compromise to your network. Many security vendors have taken this methodology on board, and their solutions can be seen to help during certain stages of an attack. I'll blog about this in more detail soon.
Thursday, 4 September 2014
iCloud Compromise...
The mainstream news has covered the compromise of iCloud, which led to a number of private photographs being exposed to the public. The first assumption was that iCloud was hacked or compromised, but Apple denies this.
Accounts Compromised...
Rather than iCloud in its entirety being compromised, the compromise was to individual accounts. It is assumed that the celebrity accounts were compromised with a brute force attack, allowing multiple tries of various passwords to each account. This meant with the right software toolset which could be acquired cheaply, numerous passwords could be tried against each account.
Simple Passwords...
It would seem that celebrities are very much like the general public when it comes to passwords. There are commonly used passwords, the top 25 of 2013 can be found here. From that article you see the commonly used passwords are "123456" and "password"! With relatively simple passwords or common words, they can easily be compromised using a dictionary attack.
Security (?) Questions...
There are many ways to recover a password. It may be requested a new password which the site or application will ask you to subsequently change. There may be a need to telephone a call centre and provide details over the telephone to reset your password. The least secure in my opinion, is the ability to answer security questions that the user has the answer.
This would seem like a secure way of resetting a password, as how many people would know your mother's maiden name, where you were born, what your favourite football team is, etc? The internet and social media has been great in many respects, but it exposes a lot of information about an individual out into the wild. Once it's out there, there is no way to control, edit or delete it. Bear this in mind if you have to use to methodology for any website or application.
It would seem that this current compromise a is new thing, but something very similar happened over nine years ago when Paris Hilton's mobile phone was hacked in 2005. How was this done? The T-Mobile Sidekick device had an internet facing dashboard. If you forgot your password, you could answer some security questions including date of birth and your pet's name. All the security questions could be answered with an internet search engine.
Complex Passwords, hard to remember?
As the levels of security have to rise, so this can only make it more difficult to use the services or applications. There is always a balance between usability and complexity. We can encourage people to use a mixture of upper and lower case, special characters and numbers, but will only mean more password resets these complex passwords will be forgotten more easily.
Also common advice is not to use the same password over multiple applications and services. This only increases the users capacity to forget a password!
Phishing...
News has come to light this morning that rather than a brute force attack, it may have been a phishing attack. We are reminded to check the legitimacy of an email before acting on it, and if it seems fishy (excuse the pun) to ignore it or delete it. Some celebrities may have fallen for one of the simplest tricks.
The bad guy sends out emails that looks like an email from Apple. It tells the user that there is some sort of issue with the account that requires a password reset/change/confirmation. The user will enter their password which is stored by the bad guy. The user will be presented with either a failed message screen, a confirmation all is OK and if they were clever, even synchronise the password with Apple, so all seems right for the user.
Two Factor Authentication...
I have written a few blog posts in the past regarding passwords and multi-factor authentication, but it's relevant to re-cap it. It we look at the different types of information that can be used to log a user in, we can take different types of information in order to increase security. So one form this can take is information the user knows, such as username, password, PINs and patterns. Another form this information can take is information a piece of technology gives the user, such as a passcode from a token, a passcode from a device such as a smartphone or computer, or a passcode set via SMS to a known mobile telephone number. If the known information and the provided information are different types of information, or factors, it becomes clear where the term two factor authentication comes from.
Free protection...
I've mentioned it before, but service providers such as Apple's iCloud, GMail, eBay and Facebook give the option to switch on two-step verification, where if you try to login from a new device, a new browser or a different country, the user will be prompted to enter a code that is sent to the registered mobile phone number. The security is there and it's free!
Increase your security posture
Be aware of the security questions you choose to to use. Are the answers to your security questions available from the likes of Facebook and Twitter?
Be aware of emails asking for password changes. Double check with the service provider.
If you want to use more complex passwords, but are worried about remembering them all, use a password vault to store these passwords securely.
Although two factor authentication may add a slight delay to using the service, it gives a level of protection that will make it a lot more difficult to compromise your personal information, your data and in this case, your personal photos.
Monday, 1 September 2014
Are you wearing a security risk?
Quantified Self
The "quantified self" is incorporating technology to capture data on various aspects of a person's life. This could be food and water intake, blood pressure, glucose levels, steps, movement, sleep patterns and such like. As these wearable monitoring solutions become increasing popular, there needs to be an understanding as to how some of the more mainstream technology works.Data Connectivity
Many of these wearable devices will collect data, and then synchronise to a computer or smart device using Bluetooth LE (low energy), sometimes known as Bluetooth 4.0. Data can be manually entered onto the computer or smart device. This data will then transferred to a cloud location giving a dashboard with history, via an internet connection whether that be cellular, wireless or cabled.FitBit & Security?
I recently purchased a FitBit Flex, which is a wearable band which monitors my steps, movement and sleep patterns. So I wanted to look at this example and if there were any security risks I should be aware of.Personal Information
First of all I needed to create an account on a web portal, which required either a login using Google or Facebook credentials or create a login with an email address. The portal uses SSL certificate, although there is no stipulation for a strong password.Personal information can be stored, but it's not mandatory. There is the ability to store your name, postal address, gender, date of birth, country, height and weight. The dashboard can create API links to Facebook, Twitter and WordPress.
The dashboard shows the number of steps taken, distance covered, and then give a calculation of calories burnt.
Bluetooth Wearable
The wearable is charged up and ready to go what next? It will start to collect data and that data will need to be transferred to a smart device or computer. The wearable will use Bluetooth LE, as this will have a minimal battery drain on the smart device. The wearable synchronises with the computer or smart device using the software or app installed. Although the wearable device is visible as a Bluetooth device, I was unable to connect to it.
I'm not suggesting that it's not possible, as Bluetooth hacking tools are quite inexpensive, but it certainly wasn't possible with a simple connection.
Dashboard Access
As mentioned before, the dashboard runs as a secure website using an SSL certificate to protect it. The credentials to log into that dashboard are either social media or an email address with password. No complexity was required on the password, despite the personal information that could be stored.
If someone had access to my email or my social media accounts, then access to the dashboard would be relatively straightforward. On my laptop with my profile, when I access the main website, it takes me straight into the dashboard.
Data Synchronisation
The data sent to the portal seems to be protected and not being transferred in clear text. There may be some concerns with the connection method used to transfer this data, so the normal rules would apply. If there is an open wireless connection, or a connection using WEP to protect it, the data can be gathered during the transfer. Whether the data would be of any use is a different matter.
If web proxy solution is being used, which is able to decrypt the traffic to websites, then some information could be gathered by these systems, where the systems administrator will have access.
I'm not too familiar with cellular data transfer, so I am unable to comment on how secure this data transfer method would be.
Data Privacy?
Another concern is whether my data privacy is being respected. Will FitBit sell my data to highest bidder? Who will have access to my data? How is it stored? How is it protected?Here is the privacy policy for UK users: https://www.fitbit.com/uk/privacy
Should I use my wearable?
As we have learnt from some very high profile breaches, no organisation or website is 100% secure. Be aware of what data you are putting on internet, but I will carry on using my FitBit Flex in the mean time.
Saturday, 30 August 2014
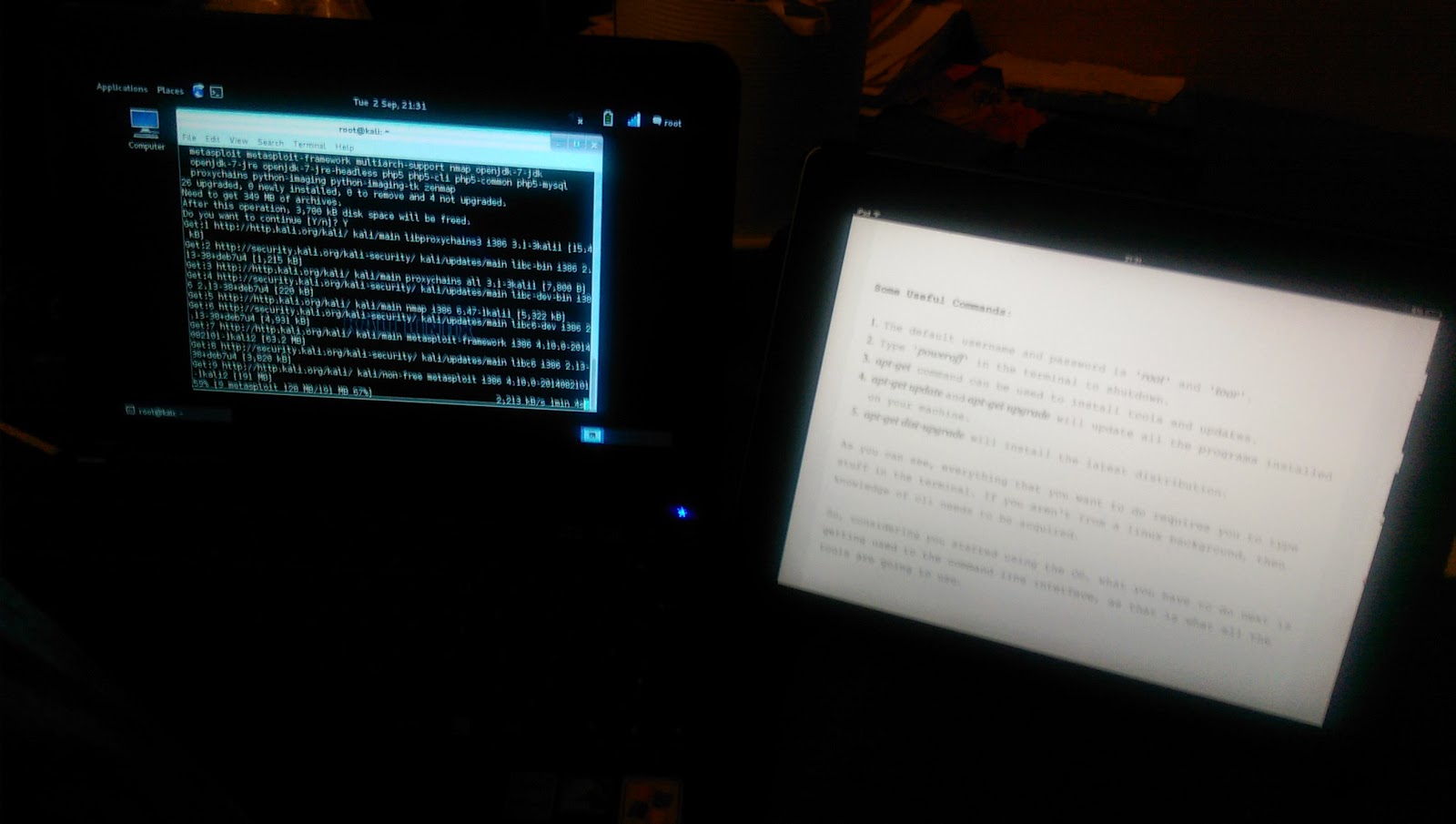
Kali Linux - Installed, what next?
As The X-Factor returns to UK television, I needed to find something else to occupy my time!!
I found a Kali tutorial site called kalitoutorials.net which is great at explaining how and why. I started with the basic commands, then started to look at how to hack WEP wireless networks. I used the toolsets to see what they can do and how the results are displayed. As my wireless network is running WPA2, some of these tools don't work.
My next job is the create a a new wireless network for me to hack. I have a number of wireless routers and access points I can use. Once I've set one up, I'll write a step-by-step guide with what I've learnt. I will state now, DO NOT hack any wireless networks that are not yours, or you do not have the expressed permission of the wireless network owner.
Tuesday, 26 August 2014
Kali Linux - Getting Started
Being a newbie to penetration testing, I was introduced to BackTrack a few years ago, but struggled to find time to investigate further.
After a few years, I now look after a team of engineers and penetration testers, so it seems like an opportune time to take a Kali.
Digging through some old hardware, I managed to get a working netbook from a couple of non-working netbooks. One started life as an MSI Wind U100 and the other an Advent 4211C. These are relatively low powered machines, with the first generation of Intel Celeron 1.6GHz processor, 1GB RAM and 80GB SATA hard drive. They are compact with their 10" screens, and the keyboard although a little smaller than most laptops, perfectly usable.
I have made some modifications to the hybrid device, which include an additional 1GB RAM, bringing it up to 2GB RAM. I've also changed the existing 80GB 5400RPM SATA hard drive for a 40GB Intel SDD, which I hope will extend the battery life of the machine and reduce the amount of heat it generates. Talking of batteries, the standard 3-cell battery is appalling, so this has been replaced with a 9-cell battery from ebay, so the battery life is now beyond 5 hours, rather than less than an hour!
With the hardware in place, the next step is to get the software installed. There are some well written instructions to get the Kali Linux installer on to a USB stick here: http://docs.kali.org/installation/kali-linux-live-usb-install
Once the USB stick has been created, I ensured the computer would boot from a USB stick and let it install onto the computer. If you have some experience with installing Linux, such as Ubuntu, then this will seem very familiar. If you have a Windows background, you can probably muddle your way through (I did when I first tackled Ubuntu!)
After a few years, I now look after a team of engineers and penetration testers, so it seems like an opportune time to take a Kali.
Digging through some old hardware, I managed to get a working netbook from a couple of non-working netbooks. One started life as an MSI Wind U100 and the other an Advent 4211C. These are relatively low powered machines, with the first generation of Intel Celeron 1.6GHz processor, 1GB RAM and 80GB SATA hard drive. They are compact with their 10" screens, and the keyboard although a little smaller than most laptops, perfectly usable.
I have made some modifications to the hybrid device, which include an additional 1GB RAM, bringing it up to 2GB RAM. I've also changed the existing 80GB 5400RPM SATA hard drive for a 40GB Intel SDD, which I hope will extend the battery life of the machine and reduce the amount of heat it generates. Talking of batteries, the standard 3-cell battery is appalling, so this has been replaced with a 9-cell battery from ebay, so the battery life is now beyond 5 hours, rather than less than an hour!
With the hardware in place, the next step is to get the software installed. There are some well written instructions to get the Kali Linux installer on to a USB stick here: http://docs.kali.org/installation/kali-linux-live-usb-install
Once the USB stick has been created, I ensured the computer would boot from a USB stick and let it install onto the computer. If you have some experience with installing Linux, such as Ubuntu, then this will seem very familiar. If you have a Windows background, you can probably muddle your way through (I did when I first tackled Ubuntu!)
All being well, you will end up with Kali Linux installed on your computer. The only issue I had was that my hidden wireless network could not be picked up during the installation, so I reverted to using a network cable to complete the installation, then configuring the wireless settings after the installation had completed.
The next step is update the software and then start learning how to use Kali!
There is some great documentation here: http://www.kali.org/official-documentation/
There is also official training here: http://www.offensive-security.com/information-security-training/penetration-testing-with-kali-linux/
Monday, 18 August 2014
Cloud Security - Best practice [Link - Cloud Security International]
Here's an article I was asked to write about Cloud Security best practices:
http://cloudsecurityinternational.info/news_full.php?id=34649&title=
http://cloudsecurityinternational.info/news_full.php?id=34649&title=
Wednesday, 30 July 2014
Happy 5th Birthday
I started this blog five years ago to keep track of issues and workarounds I was seeing when I working with specific security solutions. As my role has changed, so has the content, it's moved from a "Notes from the field" to a more "Security Social Commentary" blog.
Although it started as a technical blog, it was always important to me to keep it clear. When it was fixing an issue, I should be able to explain both the issue and the fix. As I move forward to look at the latest news about compromises and breaches, I've tried to keep it simple by explaining the issue and how it can be fixed or avoided.
So Happy 5th Birthday blog.andytang.com!
Although it started as a technical blog, it was always important to me to keep it clear. When it was fixing an issue, I should be able to explain both the issue and the fix. As I move forward to look at the latest news about compromises and breaches, I've tried to keep it simple by explaining the issue and how it can be fixed or avoided.
So Happy 5th Birthday blog.andytang.com!
Monday, 28 July 2014
Hacking humans...
There is undoubtedly more news coverage on security breaches
or hacks into some well-known companies.
When large retail chains like Target in the States, or
massive online websites like eBay get breached, the
concerns about losing data and the impact on the consumer is massive.
Technology will protect us…
There are many technical solutions that can protect organisations, from traditional security solutions such as anti-virus software, web filtering solutions, email filtering solutions, firewalls, intrusion detection and prevention, encryption, secure authentication and endpoint lockdown solutions. There are new technologies, which use sandboxing technologies, behavioural analytics, data analysis tools, and next generation technologies refining and enhancing the traditional security solutions.
With all these solutions in place, it would be difficult to
believe that organisations are still being breached, but yet most of these technologies are in and running in these organisations. These systems are not infallible as a number of technical solutions were subject to a major security flaw, when the Heartbleed bug was highlighted.
Legislation will protect us…
There are many legislations when looking at Information Security, but although many are there to protect information, such as the Data Protection Act, Freedom of Information Act, Privacy and Electronic Communications Regulations, Computer Misuse Act, Terrorism Act, Official Secrets Act, Malicious Communications Act and even the new Data Retention and Investigatory Powers Bill.
Although these acts look after the information of the individual, an organisation or what the people can see, these are not safeguards to protecting organisations. These legislations would have done little or nothing to prevent the breaches that typically occur.
ISO 27001 and ISO 9001 are framework standards which can help safeguard the data through good practices, as can the PCI standard, but again organisations can adhere to these standards and still face the organisation being compromised.
Our people will protect us…
It is commonly joked within IT departments that "the problem is between the chair and the keyboard", implying that users are the weakest links. It's not surprising as social engineering and more targeted attacks have the "look and feel" of legitimate communication. When a large security organisation like RSA is breached it brings into question the users education. In this situation, the spear phishing (specifically directed email) attack was launched and captured by the organisation's email SPAM filter. The technology had worked, but the release of an important looking email and clicking on it, gave way to a breach that reportedly cost RSA $66 Million.
It is also believed that only 11 malicious spear phishing emails were received, all of which were caught by the SPAM filter, but it only took one person to instigate this PR nightmare.
User Education
It is often said that all compromises have used elevated privileges, which means the threats are targeting individuals because they have specific administrative rights or access to specific system. Do not overlook the importance of user education and awareness.
The technology may to there capture some of the security threats, and legislations to help safeguard practices, but vigilant and well trained users will help organisations more.
Wednesday, 16 July 2014
Data, data, data...
There are many terms thrown around about data, such as big
data, data privacy, data protection, data compliancy and data security.
Generating more and more data
The volume of data gathered is ever increasing, whether it’s
in the commercial world or our personal world.
As ways of generating data increases thorough social networking, photos
get larger through greater megapixels, the number of internet connected devices
we carry increase from zero to three or more, as media such as books, magazines
and music become digital, we can readily see why there has been phenomenal
growth in data generation.
With the many streams of data we generate and have access to,
the challenges of collecting, manipulating, aggregating this data become all too
apparent, and these are the challenges of big data.
Keeping it private
With all this data, there should be concerns with who sees
it. Ensuring the necessary controls are
in place can be difficult, whether it’s who sees our photographs on a social
media site, or when data leaves a controlled environment and into uncontrolled
public cloud storage facilities.
Most people don’t want their personal information made
public. This may be home addresses,
email addresses, telephone numbers, passport numbers, etc. This is the sort of information most people would
like to keep private.
Keeping data where only the right people, can see the
right information, but ensuring the privacy of that data is maintained, are the
challenges of data privacy and data protection.
Law enforcement
There must be laws in place to protect information. There are a number of legislations
to protect us, along with industry bodies policing certain industry
verticals. If these legislations or compliance
bodies are ignored or contravened, then fines or dismissal can be the penalty.
Using the legal system or industry bodies to monitor and
police the data, could be considered data compliancy.
Technical Enforcement
There are many technical solutions that can help protect the
data, whether it’s by encryption, password protection, two factor authentication
access, VLANs, data segmentation, database security solutions, data leakage
prevention solutions, etc.
These solutions are just that. It is more important to understand the
challenges and issues, before jumping in with a technical solution.
CIA?
Working in Information Security, many people will refer to
the CIA triad. This is where Confidentiality, Integrity and Availability
are considered the cornerstones and core principles of Information Security.
The considerations will all data, are:
Confidentiality – Define and enforce the appropriate access
controls to the data
Integrity – Ensure the data has not been manipulated from
when it was captured
Availability – Ensure the data is accessible when it is
required
Emergency Data Laws in the UK
Currently in the UK, emergency data laws are being
rushed in. The reasons for needing
to capture this data is important for national security. The concerns are speed with which legislation
has been passed, as with many IT projects, when they are rushed, they either go
over budget, or elements are overlooked.
There is vast amount of data that will need to be collected,
aggregated, stored and interrogated. There
will also be a need to protect the various databases holding this data, and the
need to encrypt this data, so if it were to leave this environment, it would be
unusable.
This data will need to be made available, so there will be a
need to keep this data in multiple locations, but also ensuring the data that
has been captured has not been manipulated maintain the data integrity.
The biggest concern should be confidentially. There have been many reports of lost data,
inappropriate access to data, but the rise in the reports of hacking leading to
the exfiltration of data from government sources.
Data is important in
our lives, but let’s ensure that our data is protected correctly, whether it's held by a social networking site or by the government.
Wednesday, 25 June 2014
Two Factor Authentication Revisted
Passwords are not secure
I talk about two factor authentication (or 2FA, as the kids and marketing people are calling it) a lot and with good reason, passwords are not secure!Sites like this give you an insight into how secure your password is:
https://howsecureismypassword.net
It also rightly states that sites can steal your password, and if they have it, it doesn't matter how strong it is they know it. It doesn't matter if my password takes seconds or years to crack, if the bad guys have it, they don't need to crack it.
What are the factors for authentication?
Authentication can be made up of multiple factors, and by using more than one of them (hence the term, two factor authentication) you are adding security and making it difficult for the bad guys to log in as you. The following are the factors:- Something you know
- Something you are given
- Something you are
- Somewhere you are
Something you know
This will include usernames, passwords, PINs, patterns, etc. This is information you could give to someone else and they could login as you.
Something you are given
If you have a bank account with one of the major banks, you will probably have a physical token or software token, which generates a seemingly random string of number. This is creating an OTP (or One Time Password) which has a limited lifespan before becoming invalid. This means that it can only be used in that moment in time. The OTP can also be delivered via SMS or telephone call.
Something you are
This is where we move into the realms of biometrics, where fingerprints, iris scans, voice scans, etc are used to authenticate you.
Somewhere you are
There are solutions that work in conjunction with GPS devices to locate you in the world, so that you are only able to login if you are in a specific area.
Two Factor Authentication as we know it
For two factor authentication, we traditionally work with the first two; Something you know and Something you are given. This is where to access the solution, you would need to provide a username, a password and an OTP. This is something I have been advocating for over eight years, as if I have your password I can login as you. With two factor authentication running, I would also need access to the device or software that is generating the OTP.Many high profile hacks have been done using administrative passwords, but if these were coupled with a OTP, it would have made it a lot more difficult to achieve.
Why use two factor authentication?
We understand the importance of it when it comes to money, so it's a given we should be using it for banking. In fact, many online gaming sites can issue tokens to secure your gambling or your online gaming persona.I use social media, where I use Facebook for family and friends, I have two Twitter accounts (one for work and one for play) and I use LinkedIn for work. All of these outlets say something about me, so if they were compromised, there would be a reputation issue I would need to tackle. Like most people have web based email and although there is nothing too precious there, I wouldn't necessarily want it opened up to all!
Who can offer two factor authentication?
Google: With the Google ecosystem, you have one password for a number of applications, so Google offer two factor authentication, whereby they will send a code to you via SMS. This is used in tandem with your username and password. It will mean that you will need your mobile with you to access the applications, but it saves having to carry additional tokens. http://www.google.com/landing/2step/LinkedIn: My professional profile is on this site, so the last thing I'd want is for it to be tampered with, so fortunately LinkedIn also offer the SMSing of a code to your mobile phone before you can login as you. http://blog.linkedin.com/2013/05/31/protecting-your-linkedin-account-with-two-step-verification
Facebook: Although this is less critical, I won't want people being able to manipulate my profile. I know Facebook have some good measures in place around logging in from countries you don't traditionally login from, but you can add two factor authentication for browsers that you haven't login from before. https://www.facebook.com/note.php?note_id=10150172618258920
These are just some examples of commonly used sites, but remember passwords are not secure. If we know this as a fact, why aren't more sites offering two factor authentication?
If you are looking to protect remote access solutions, internal applications, operating systems or even public cloud application, all of these can be protected with third party solutions provided by MTI.
Thursday, 12 June 2014
CISSP and CPE Credits...
I know a few colleagues and friends have passed or looking at doing their CISSP (Certified Information Systems Security Professional) from the ISC2 (International Information Systems Security Certification Consortium). There are two common questions when people find out I'm a CISSP and they are; what books or course did you use? and how easy is it to maintain your CPE (Continuing Professional Education) credits?
I read a few books during my studies, but the ones I would recommend are Eric Conrad's books. I used the CISSP Study Guide (Second Edition) for my main reading, which I supplemented with the Sybex CISSP Study Guide, when I needed to read about a topic is a different way. I found Eric Conrad writes is a technically minded way, which I mean it's written for someone with a technical background. We often don't need the stories and the "fluff" used to pack out study guides making then 1,500 to 1,600 pages! The Eric Conrad book is just over 500 pages which great when you still have a full time job to do as well.
I used the Exam Cram CISSP Practice Questions to test and validate my newly learnt knowledge. I also used the questions available from Eric Conrad's companion site. On the run up to the exam, I used Eric Conrad's Eleventh Hour CISSP: Study Guide. I hold Eric Conrad in high regard even though I've never met him, without his study guides, I'm not sure I would have passed the exam.
When you have passed the exam, you have to be in good standing and maintain CPEs by continuing your education. If you work in IT Security, you should been keeping up to date regardless of the CISSP! I have managed to complete 3 years of required CPE credits in less than six months!
I work in the "channel" which means I have interaction with my vendors regarding security solutions, and have to attend a number of conferences, webcasts, training session, webinars and meetings. I also read various industry magazines to keep up to date regarding the threat landscape. Many of these activities count towards your CPE credits. I read somewhere that you only need to spend an hour a week over the three years to maintain your CPE credits.
There are regular webcasts and InfoSecurity Professional magazine from ISC2, which count towards your CPEs. Here are other resources that will count towards your CPEs:
Infosecurity Magazine
Infosecurity Europe
SC Magazine UK
Register on these sites and you will receive notifications of webcasts that will keep you up to date as well as count towards your CPEs.
Good luck if you are studying for your exam and happy reading if you are maintaining your CPEs!
I read a few books during my studies, but the ones I would recommend are Eric Conrad's books. I used the CISSP Study Guide (Second Edition) for my main reading, which I supplemented with the Sybex CISSP Study Guide, when I needed to read about a topic is a different way. I found Eric Conrad writes is a technically minded way, which I mean it's written for someone with a technical background. We often don't need the stories and the "fluff" used to pack out study guides making then 1,500 to 1,600 pages! The Eric Conrad book is just over 500 pages which great when you still have a full time job to do as well.
I used the Exam Cram CISSP Practice Questions to test and validate my newly learnt knowledge. I also used the questions available from Eric Conrad's companion site. On the run up to the exam, I used Eric Conrad's Eleventh Hour CISSP: Study Guide. I hold Eric Conrad in high regard even though I've never met him, without his study guides, I'm not sure I would have passed the exam.
When you have passed the exam, you have to be in good standing and maintain CPEs by continuing your education. If you work in IT Security, you should been keeping up to date regardless of the CISSP! I have managed to complete 3 years of required CPE credits in less than six months!
I work in the "channel" which means I have interaction with my vendors regarding security solutions, and have to attend a number of conferences, webcasts, training session, webinars and meetings. I also read various industry magazines to keep up to date regarding the threat landscape. Many of these activities count towards your CPE credits. I read somewhere that you only need to spend an hour a week over the three years to maintain your CPE credits.
There are regular webcasts and InfoSecurity Professional magazine from ISC2, which count towards your CPEs. Here are other resources that will count towards your CPEs:
Infosecurity Magazine
Infosecurity Europe
SC Magazine UK
Register on these sites and you will receive notifications of webcasts that will keep you up to date as well as count towards your CPEs.
Good luck if you are studying for your exam and happy reading if you are maintaining your CPEs!
Monday, 9 June 2014
The importance of introspective security
Hundreds of years ago, security amounted to the biggest wall that could be built. This was seen with castle walls, but as these were penetrated, additional security measures were added, such as moats and draw bridges. As these were compromised, towers with lookouts were built, then then armed guards, then the defensive measures became offensive measures with heavy weaponry used as part of the defence mechanism. These measures were in place to protect a central keep, where typically the crown jewels were kept.
Fast forward many hundreds of years, and IT security took the same attitude. Firewalls were deployed to protect the organisation, but as these measures failed or were penetrated, additional layers of security were added, in the form of anti-virus and anti-spam, when the threat was delivered within internet traffic, web content filtering was employed, then application white-listing/filtering. When more intelligent and proactive approach was required, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) were used. Despite all of these functionalities, there are still reports about breaches where the company loses its Crown jewels, their data.
(Warwick Castle - Photo by A.Tang)
Fast forward many hundreds of years, and IT security took the same attitude. Firewalls were deployed to protect the organisation, but as these measures failed or were penetrated, additional layers of security were added, in the form of anti-virus and anti-spam, when the threat was delivered within internet traffic, web content filtering was employed, then application white-listing/filtering. When more intelligent and proactive approach was required, Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) were used. Despite all of these functionalities, there are still reports about breaches where the company loses its Crown jewels, their data.
How can all this security be breached? Much like the castle, the defences look outwards not inwards. Once inside, there is rarely the same level of security in place monitoring the outbound. With Edward Snowden, he must have undergone security checks prior to beginning his contract the NSA. Although once inside it is believed that very basic and "noisy" exfiltration techniques were used to remove data. Even the NSA shows that the security is predominantly external facing, but once inside there are much lower levels of security.
The breaches from an external source typically (although there are surveys to suggest, all breaches) used privileged credentials to access the data. Not only are the threats going through the perimeter security using trusted user credentials, once in they have access to the network as the credentials will have privileged rights, the data can leave as most security solutions look at inbound, not outbound traffic.
Organisations need to look at what data is important to them, who can use it and how they are going to use it. The security should be applied intelligently to control the elements of concern, rather than tar all data in the same fashion. The protection needs to be centrally managed, but decentralised in its approach to protection. Data can reside on servers, corporate computers, removable drives, in email systems, private cloud solutions, public cloud solutions, mobile devices, tablets and these environments will be both trusted and untrusted.
The safeguards need to go beyond the firewall and our mind sets need to move on from a firewall rule mentality. We need to give much greater consideration to our data and the rights we issue to users. The protection should not only work from outside-in, but also from inside-out.
The breaches from an external source typically (although there are surveys to suggest, all breaches) used privileged credentials to access the data. Not only are the threats going through the perimeter security using trusted user credentials, once in they have access to the network as the credentials will have privileged rights, the data can leave as most security solutions look at inbound, not outbound traffic.
Organisations need to look at what data is important to them, who can use it and how they are going to use it. The security should be applied intelligently to control the elements of concern, rather than tar all data in the same fashion. The protection needs to be centrally managed, but decentralised in its approach to protection. Data can reside on servers, corporate computers, removable drives, in email systems, private cloud solutions, public cloud solutions, mobile devices, tablets and these environments will be both trusted and untrusted.
The safeguards need to go beyond the firewall and our mind sets need to move on from a firewall rule mentality. We need to give much greater consideration to our data and the rights we issue to users. The protection should not only work from outside-in, but also from inside-out.
Technologies are starting to use behavioural analysis, as this will analyse computers, users, data, time, access and many other factors to then decide if your network is under threat or not. This requires an even greater mindset change as we no longer look at rules to prevent hoping all bases are covered, but to analyse a number of actions before deciding on the appropriate course of action.
I've heard many times, it's a case of when, not if your network gets breached. If this is true and the layers are going to fail, then the requirements are to slow down the intruder and prevent the exfiltration of your data, while understanding what has occurred.
Don't think of security in terms of a castle's protection, think of it as complex maze.
Don't think of security in terms of a castle's protection, think of it as complex maze.
Subscribe to:
Posts (Atom)